1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
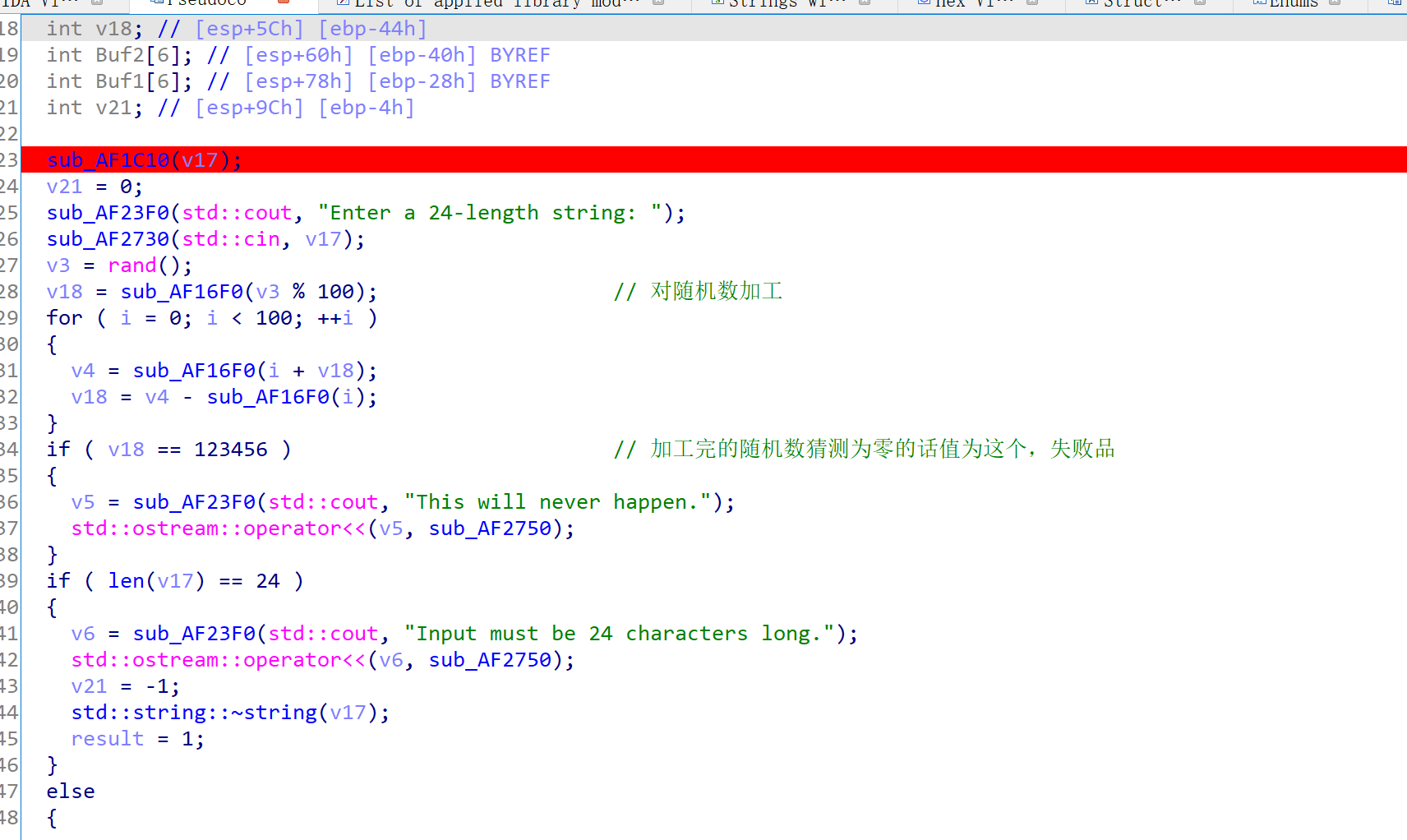
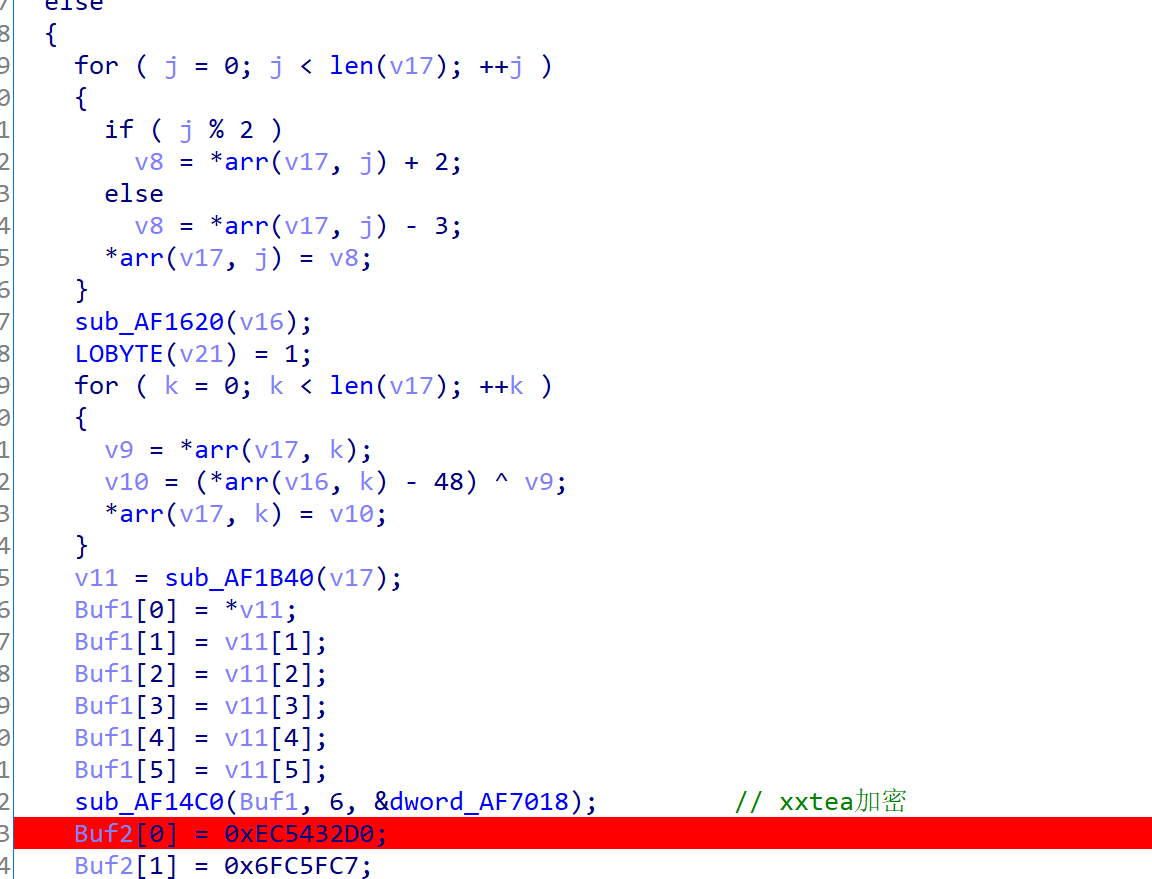
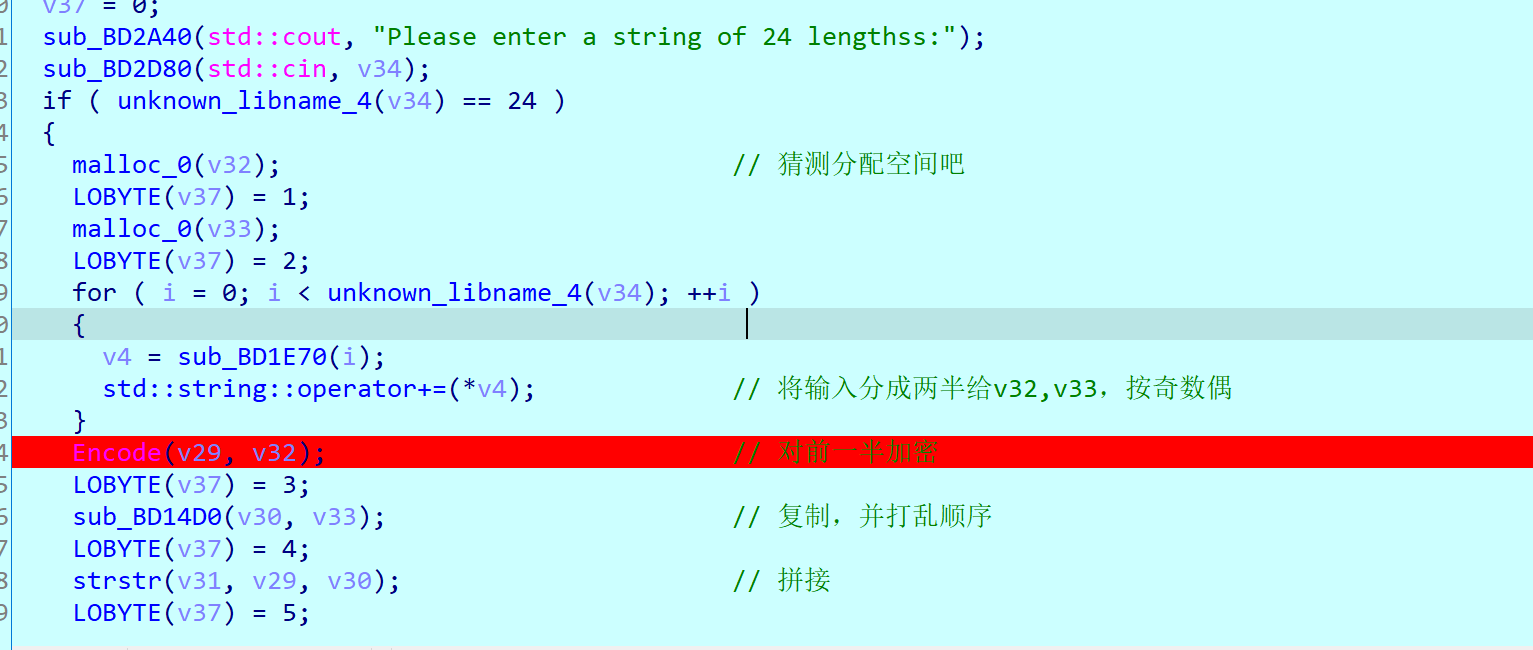
| #include"stdio.h"
#include"windows.h"
__int64 __fastcall Encryption(int *a1, int *a2, int a3);
int main(){
__int64 v9[2]; // [rsp+60h] [rbp-30h]
__int64 v10[2];
char Str[28]; // [rsp+40h] [rbp-50h] BYREF
// char v8[4];
int len;
// int arr[] = {0x69, 0xB5, 0xA2, 0x72, 0xE5, 0x67, 0xFA, 0xB,
// 0x60, 0x9D, 0xBA, 0x5D, 0x70, 0xC3, 0xB2, 0x9A,
// 0xD1, 0x2F, 0x9A, 0xB0, 0xD5, 0x16, 0x69, 0xAA,
// 0x0D, 0x34};
int arr[]={0xBB,0x63,0xF4,0x20,0x37,0x15,0xBA,0x72,0xE9,0x35,0x95,0x98,0xF7,0x34,0x36,0xE5,0xAA,0x73,0x07,0x42,0x45,0xE4,0x8B,0xBB,0xCA,0x34};
int v8[] = {0x49,0x53,0x43,0x43};
strcpy(Str, "So--this-is-the-right-flag");
len = strlen(Str);
Encryption(arr,v8,len);
for(int i=0;i<26;i++)
putchar(arr[i]&0xff);
return 0;
}
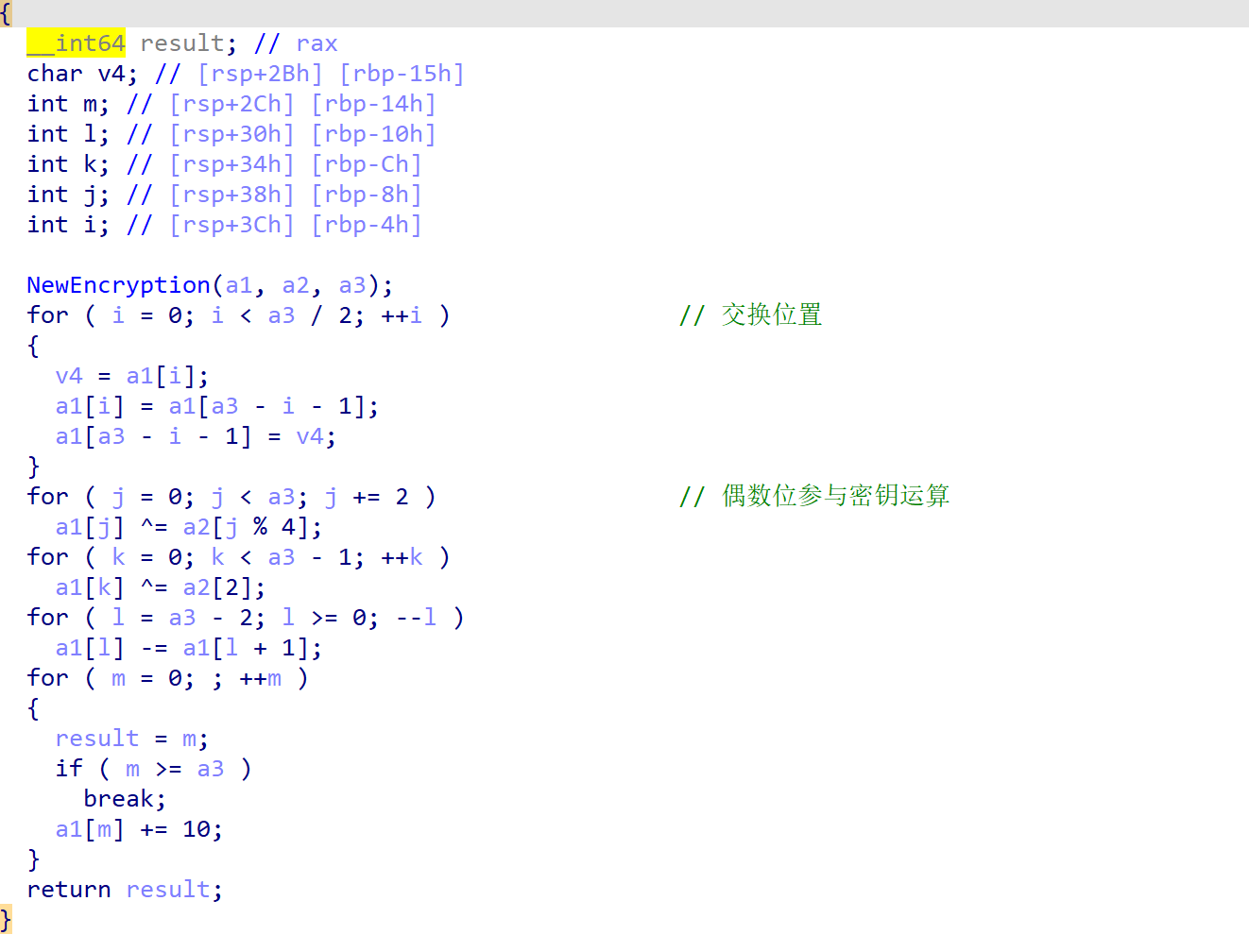
__int64 __fastcall Encryption(int *a1, int *a2, int a3)
{
__int64 result; // rax
char v4; // [rsp+2Bh] [rbp-15h]
int m; // [rsp+2Ch] [rbp-14h]
int l; // [rsp+30h] [rbp-10h]
int k; // [rsp+34h] [rbp-Ch]
int j; // [rsp+38h] [rbp-8h]
int i; // [rsp+3Ch] [rbp-4h]
/*
NewEncryption(a1, a2, a3);
for ( i = 0; i < a3 / 2; ++i ) // 交换位置
{
v4 = a1[i];
a1[i] = a1[a3 - i - 1];
a1[a3 - i - 1] = v4;
}
for ( j = 0; j < a3; j += 2 ) // 偶数位参与密钥运算
a1[j] ^= a2[j % 4];
*/
for ( m = 0; ; ++m )
{
result = (unsigned int)m;
if ( m >= a3 )
break;
a1[m] -= 10;
}
for ( l = 0; l <= a3-2; ++l )
a1[l] += a1[l + 1];
for ( k = 0; k < a3 - 1; ++k )
a1[k] ^= a2[2];
for ( j = 0; j < a3; j += 2 ) // 偶数位参与密钥运算
a1[j] ^= a2[j % 4];
for ( i = 0; i < a3; ++i )
a1[i] += a2[i % 4];
return result;
}
//ISCC{a4W,SF=^u{W/Iyu&{B#p}
|