CISCN2024之RE
Reverse
asm_re
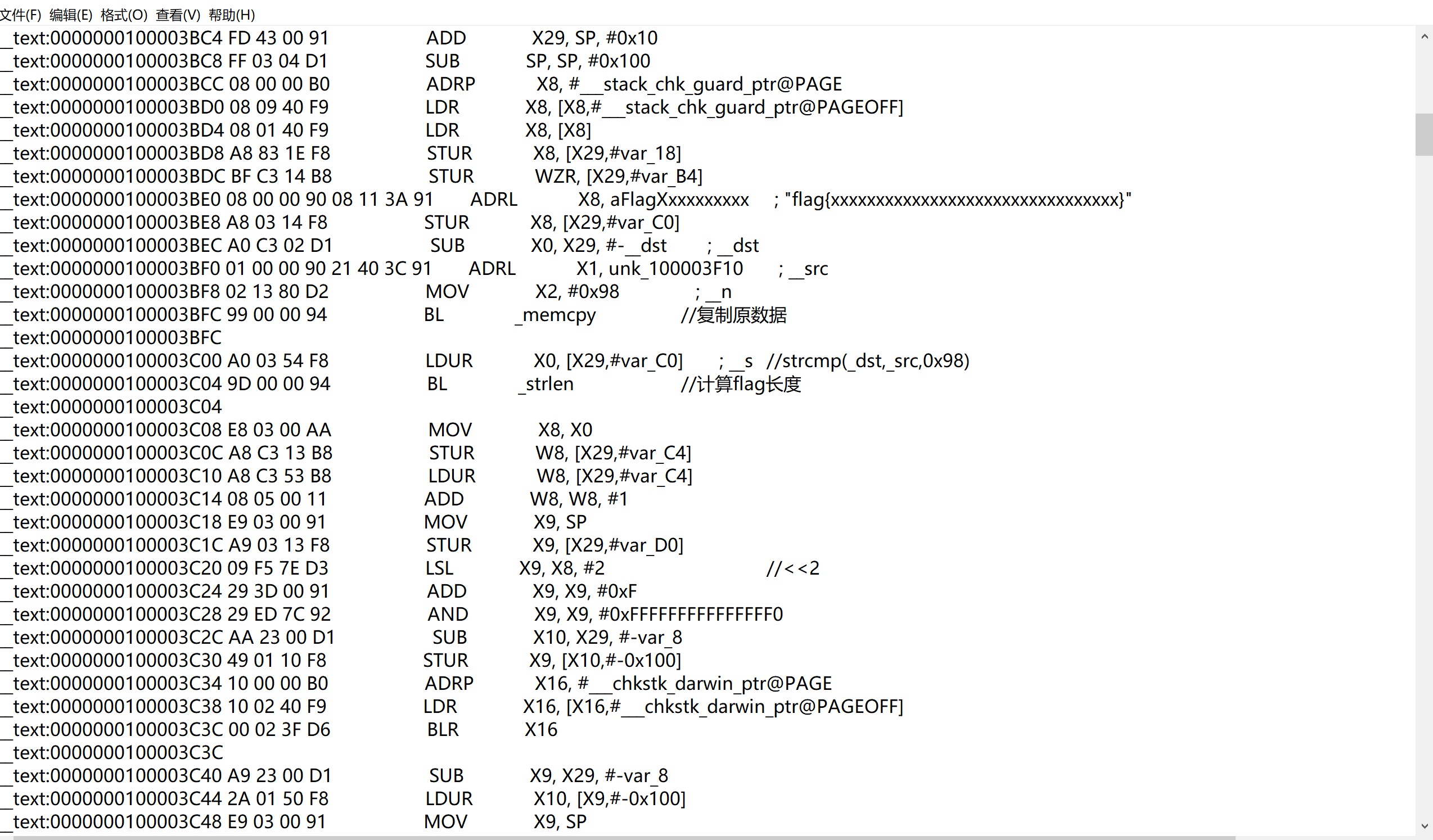
分析arm汇编发现是三个循环,一个加密flag,一个加密input,一个结果判断,前两个相同
1 |
|
gdb_debug
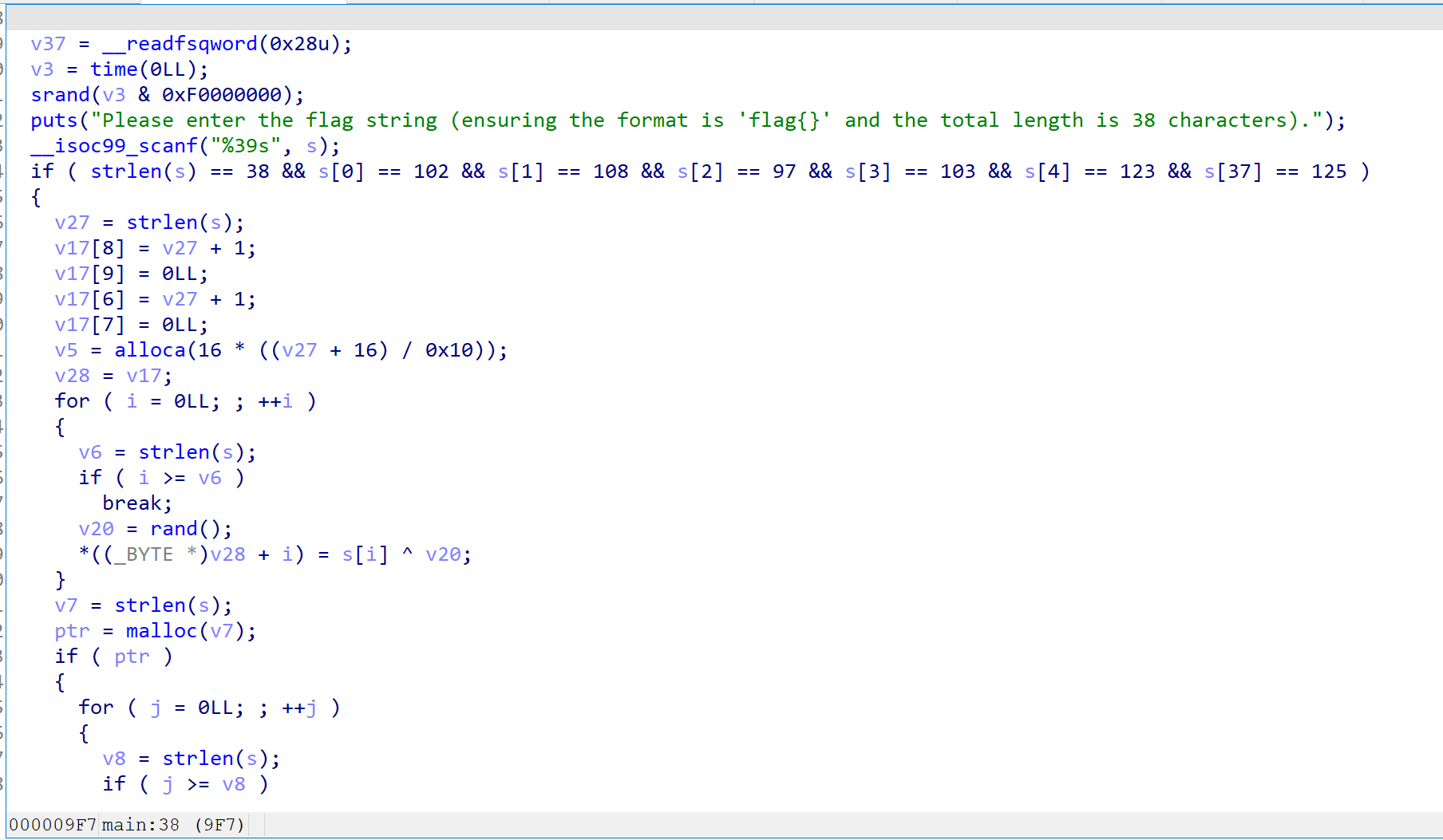
主要是随机数,虽然是时间作为种子,但是伪随机,被&掉了,然后就是产生密钥盒子等运算
1 |
|
androidso_re
这道题就是个简单的des加密,只要知道key和iv即可,至少我知道的方法中动调或者直接frida附加都可以获得运行时的参数,或者直接使用java调用库函数,动调不知道什么原因总是跑一半就断掉了,frida的环境之前给删掉了,至于函数库由于whereislib这道题用python调死调不出来,所以犹豫没有试过,什么时候自己的想法才可以完全用代码完全实现啊😟
分析
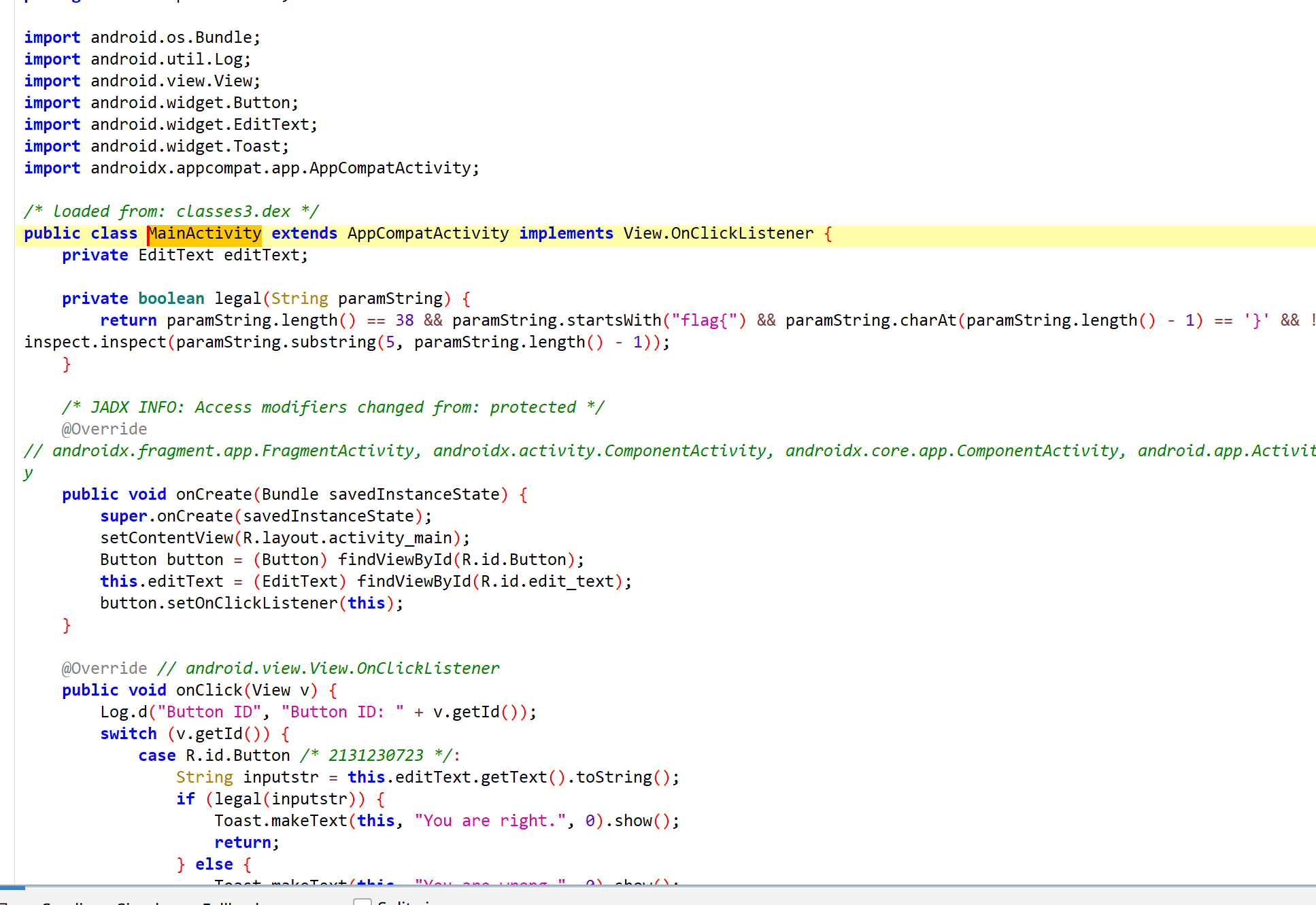
发现加密函数在inspect里面
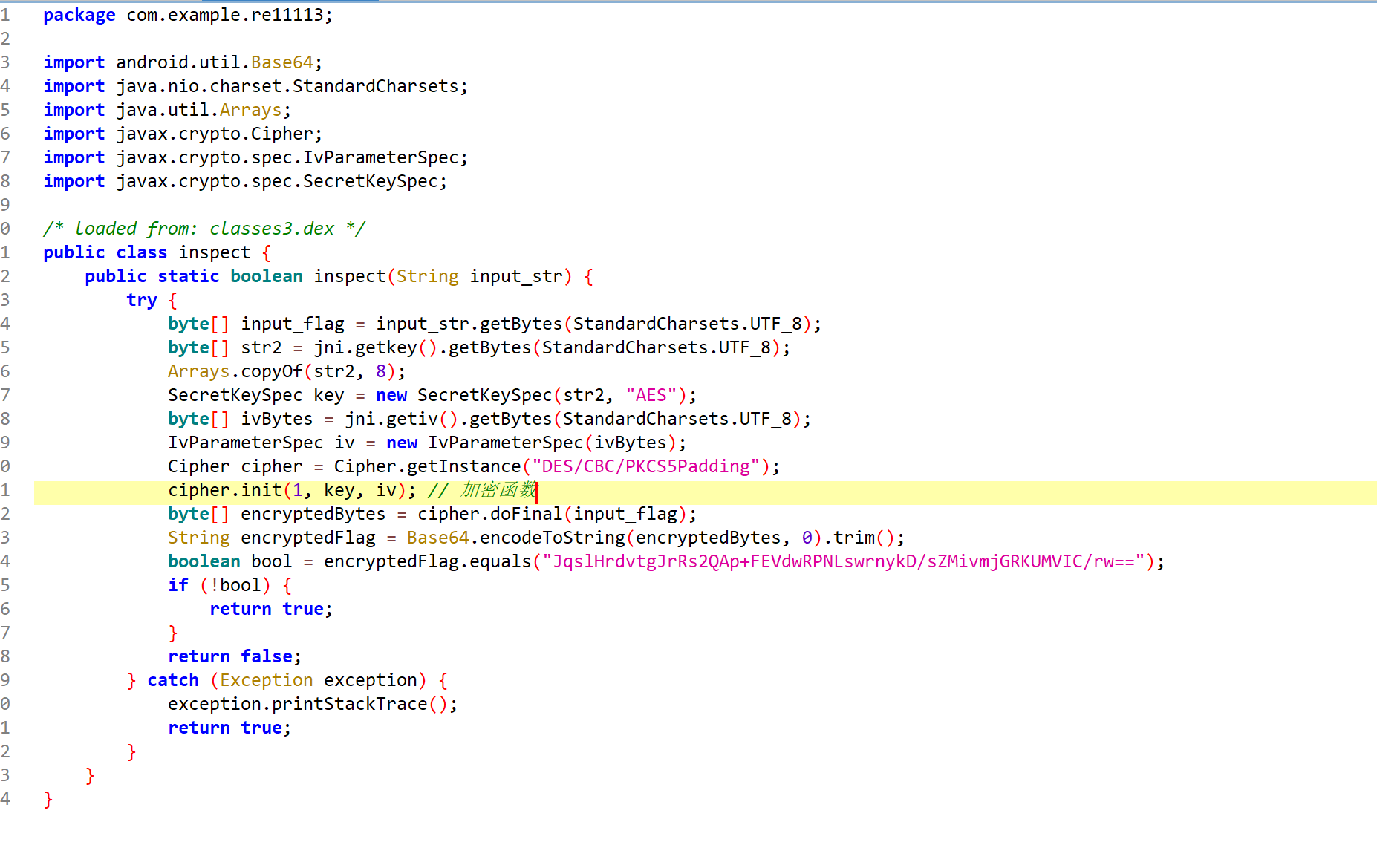
发现函数在so函数库里面
解题方法
frida
frida显示apk文件的值方法也很多可以主动调用或者等待app主动调用,利用函数覆盖和重载可以实现,本打算直接使用主动调用但一直报错,可以知道那两个函数是静态函数,但提示输入值不符合有0xbb,可能是主动调用时侯环境并没有完全被初始化完全
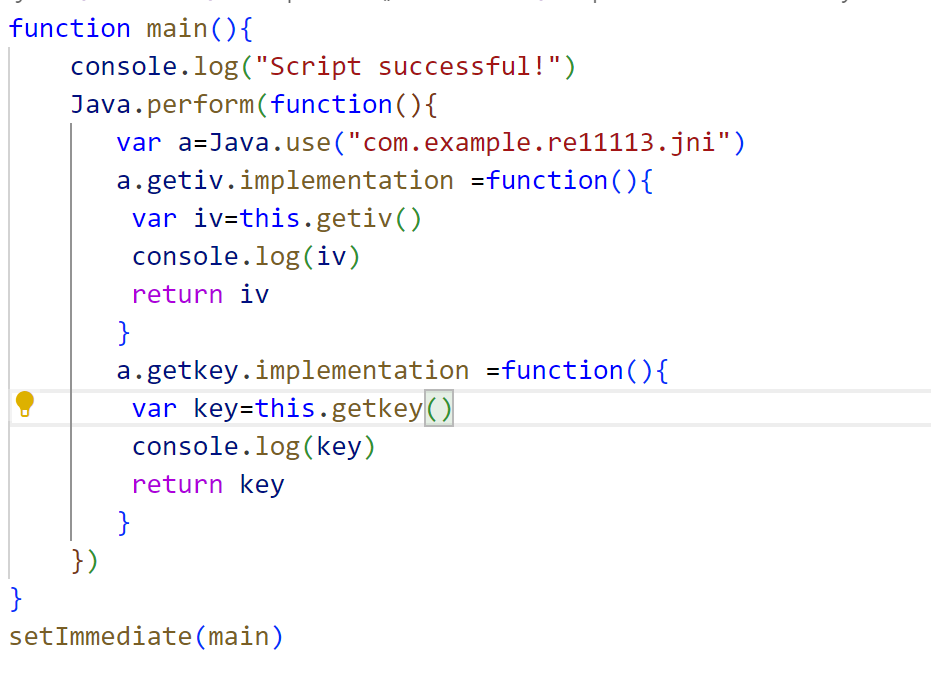
此时需要满足输入flag{***}长度为38才会调用inspect验证函数
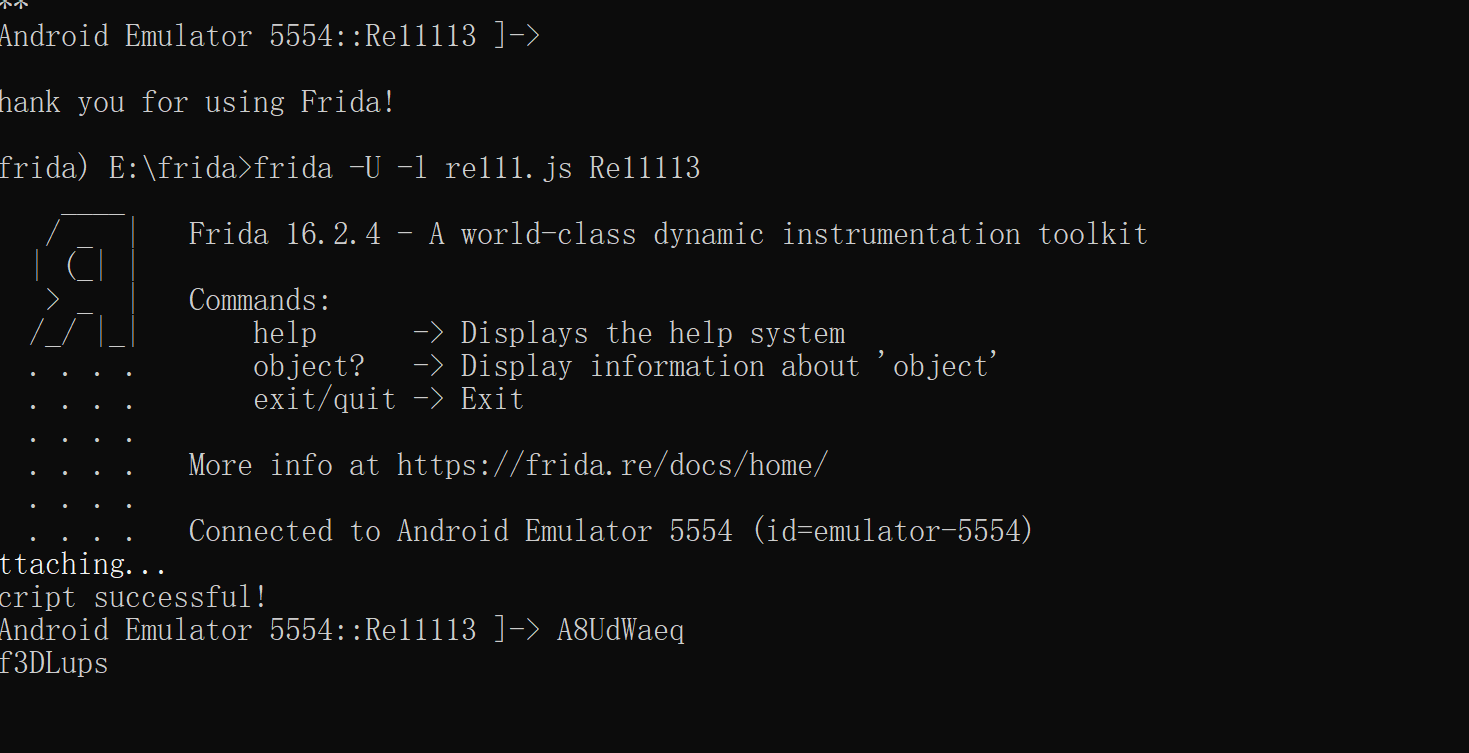
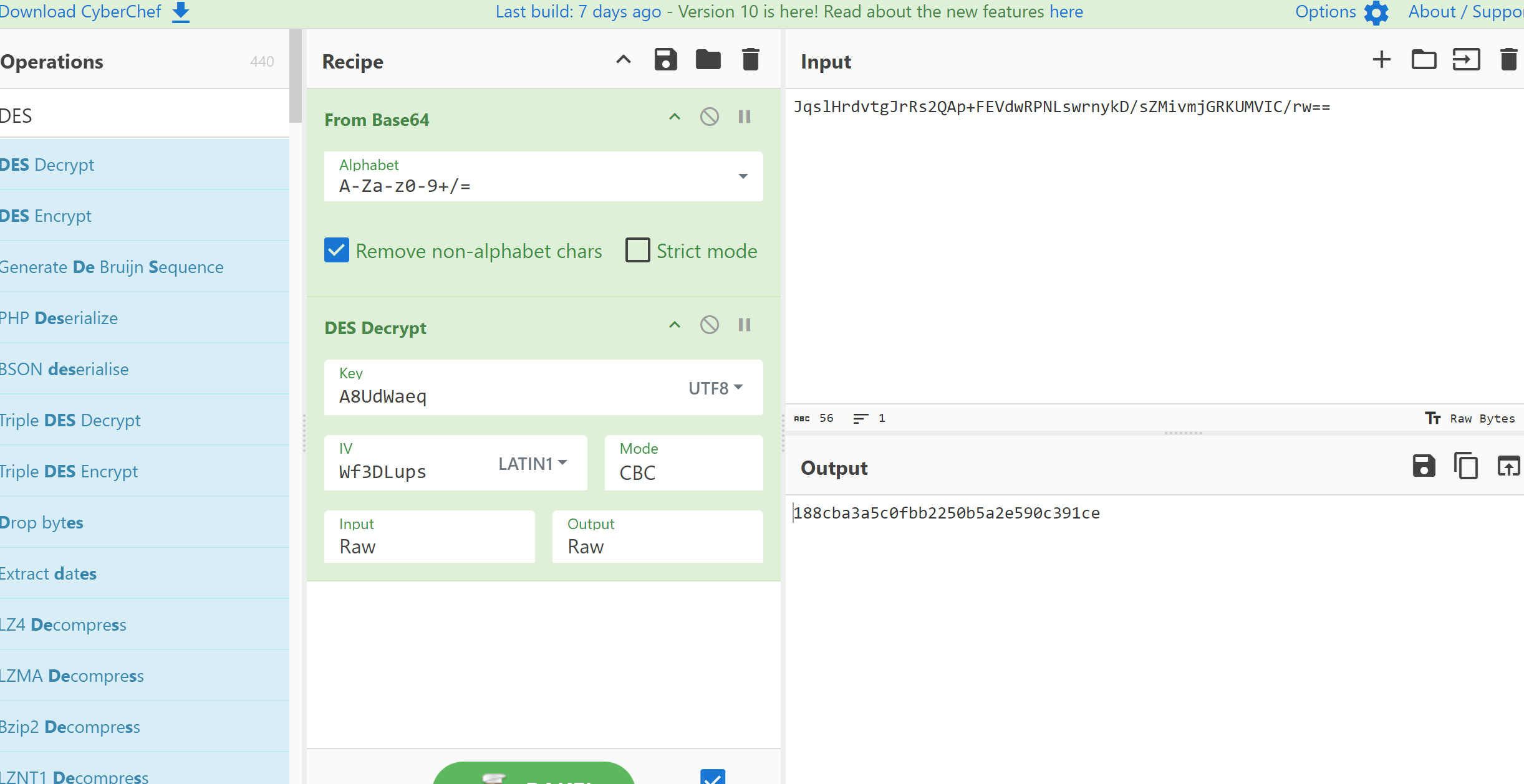
动调
ida倒是可以跑动但太乱了不好定位主要函数位置
使用jeb试试,提示java版本有点问题,jeb动调到调用so函数时会弹出,或许两个结合一下就可以了吧,先到这吧,以后有机会再试试
WhereTheLib
两种方法,一种是直接爆破,一种分析so文件
爆破
分析
文件为linux文件给定python文件需要在liunx下使用python3.10运行
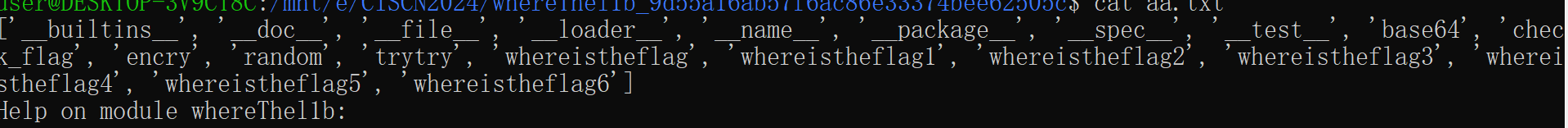
发现给定python文件调用了两个函数
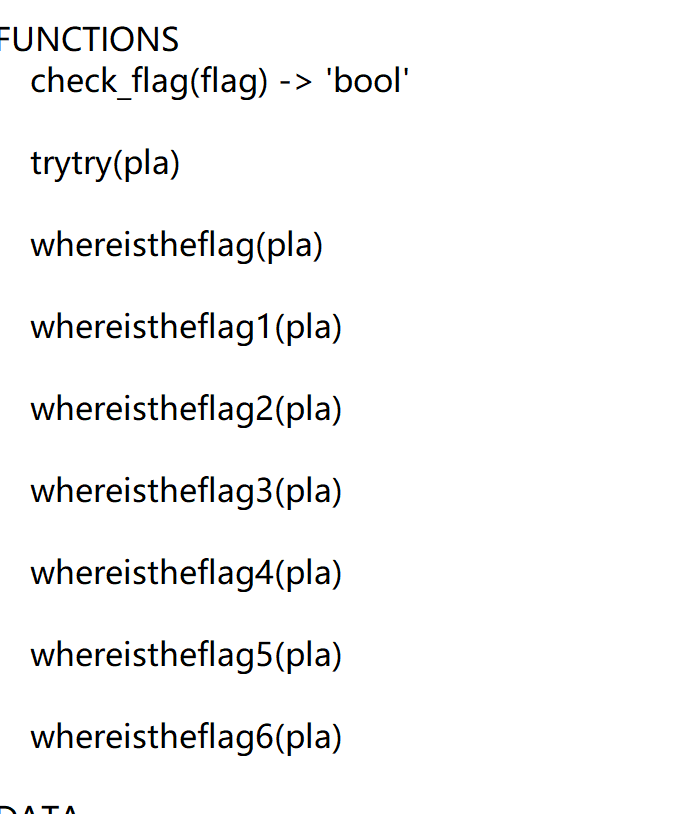
内部函数调用流程,但在脚本中whereistheflag只是返回了输入的字节串,主要加密在trytry,看so文件内部知道主要加密就是随机数和base64,三个输入对应四个结果字符输出
wp
1 | import whereThel1b |
so
谷歌一下可以知道这是一个被Cpython编译了的pyd文件(linux上为so)
分析
利用help函数和dir函数我们可以很快的直到函数主要逻辑
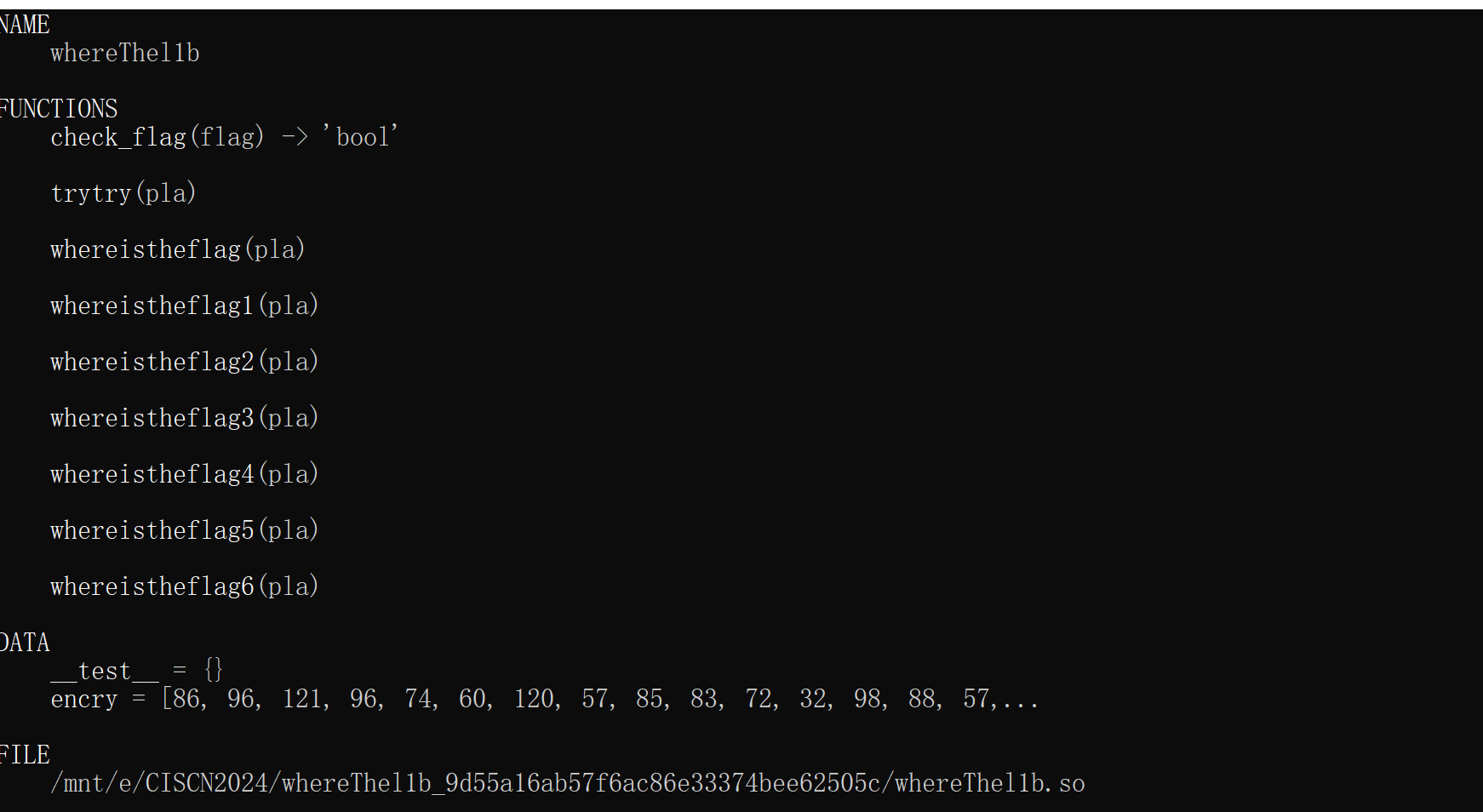
可以发现so文件中所有自定义函数和对象有这些
主要函数:
_pyx_pymod_exec_whereThel1b:初始化各模块
_Pyx_CreateStringTabAndInitStrings: 是 Cython 在其编译过程中生成的一个内部函数,用于初始化和管理 Cython 模块中使用的字符串字面量。
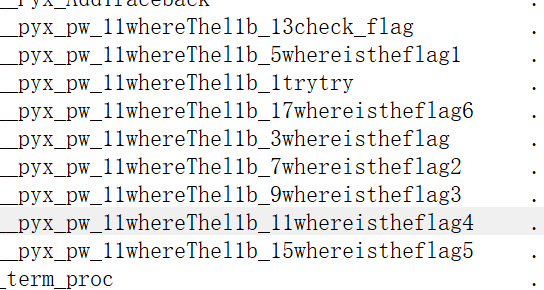
check_flag:验证flag是否非空
trytry:发现设置了seed
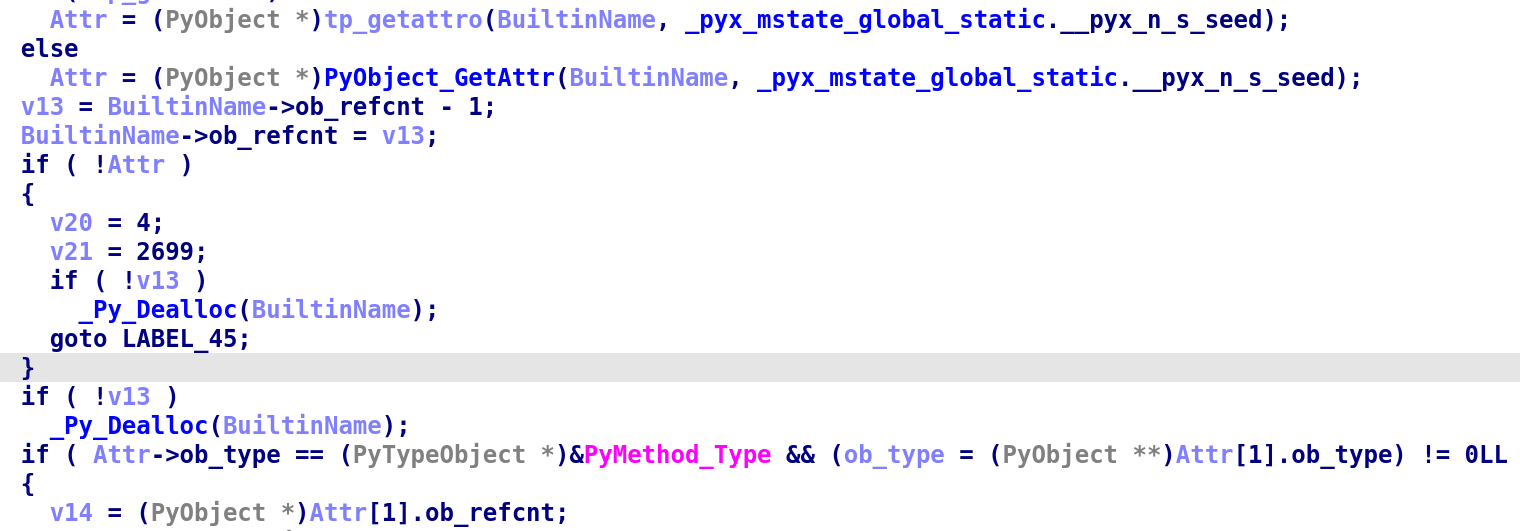
当时没以为下面if判断的值为0是seed,因为感觉是类型更像是一些系统跳转什么的,而且下面有一个一样的·
whereistheflag:发现调用了randint
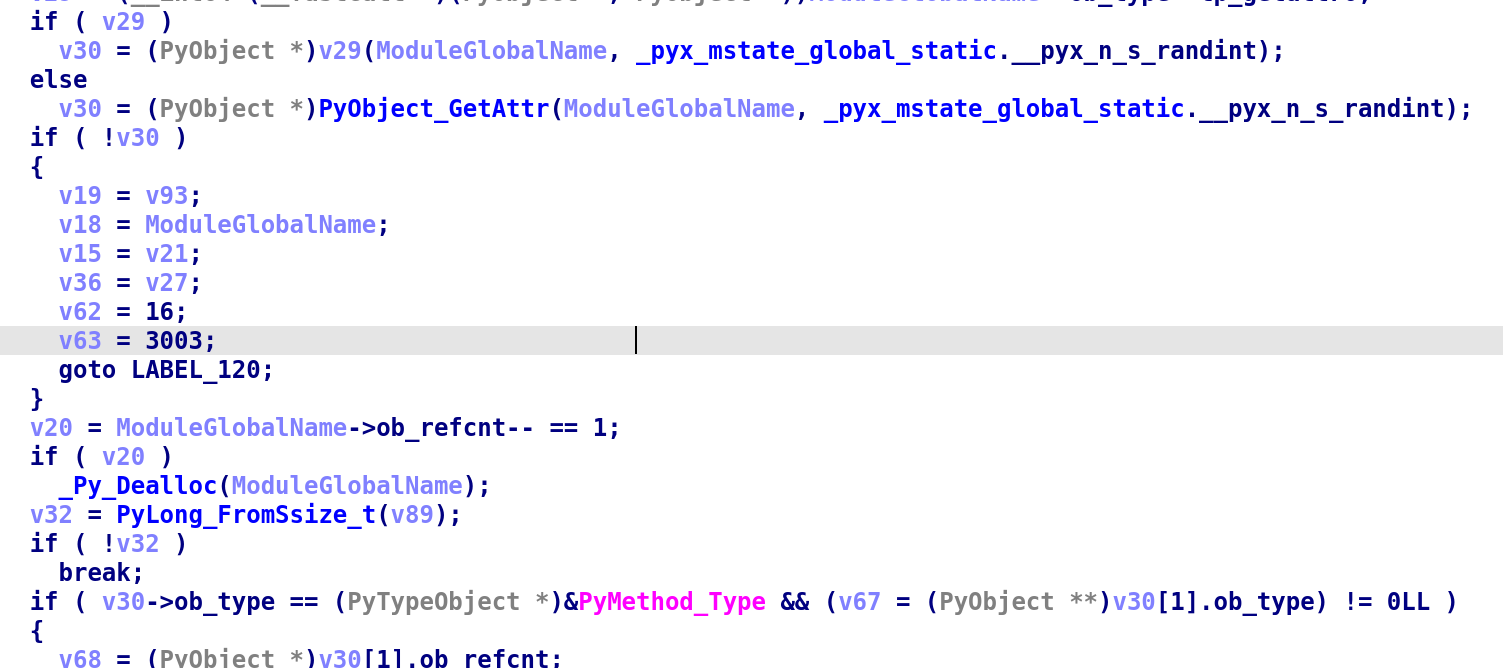
当时看到有xor运算
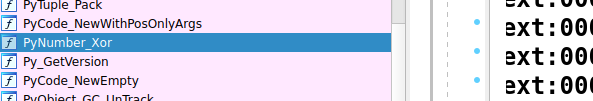
这倒很容易猜出来
但即使是现在面向结果解题感觉还是很难想象出来是这么个解题思路
wp
1 | import base64 |







